Next: 5 Lessons Learned Up: Appnotes Index Previous:3 RASSP Manufacturing Interface Usage Scenarios
![]()
![]()
![]()
![]()
Next: 5 Lessons Learned
Up: Appnotes Index
Previous:3 RASSP Manufacturing Interface Usage Scenarios

| =Represents the physical file system location for the items residing in the associated vault (shared workspace) or user (private workspace). Vault and work locations may be on the same host machine or on seperate machines wihin a network. VL=Vault Location: Each vault location will be associated with only 1 vault. WL=Work Location: Each work location will be associated with only 1 user.
|
| =Represents a DM2 saved query. SQ=Saved Query: Every user will have access to the Global Workspace through a pre-defined query.
|

| =Represents a logical collection of objects based on ownership. An owner of an object is either a user or a vault. Each vault will have 1 or more vault locations associated with it. Each user may be associated with 1 or more vaults. Each user will have 1 or more work locations associated with it.
|
A global workspace in AIM is mapped to all baselined objects in all vaults within a database. Items are visible in a global workspace by use of the AIM Saved Query Object Class. Shared workspaces in AIM are mapped to a vault/vault location and can be accessed by performing transfer, check in, and check out operations. A vault is a logical collection of shared objects. A vault may contain data objects or actual file system items. A vault location provides a file system location for storing physical files owned by the vault.
In AIM, each user has a private workspace. Based on projects, a parent-child relationship can be established between private and shared workspaces. A private workspace may have more than one work location. Similar to vault locations, a work location provides actual file system space for objects residing in a private workspace. Note: A private workspace may have relationships with more than one shared workspace.
AIM provides out-of-the-box implementation of the RASSP Authorization model by using the AIM feature of message access rules. Message access rules are granting in nature. An explicit rule must exist for an action to be performed on an object class. If a rule exists, then the actions granted by the rule cannot be limited by another rule. In AIM, if two or more rules conflict or overlap, then the more permissive rule is always followed. Due to the object-oriented nature of AIM, inheritance plays an important part in maintaining the authorization hierarchy. Message access rules may be inherited throughout the AIM data model.
In addition to class and rule authorization, AIM provides additional enforcement of the RASSP Authorization Model by allowing roles to be divided into various groups of users. By dividing the users into five types of groups, administrative authority is distributed over the entire RASSP System. Figure 4 - 2 depicts the design of the RASSP Authorization user group hierarchy, and the association of the roles to the workspaces.
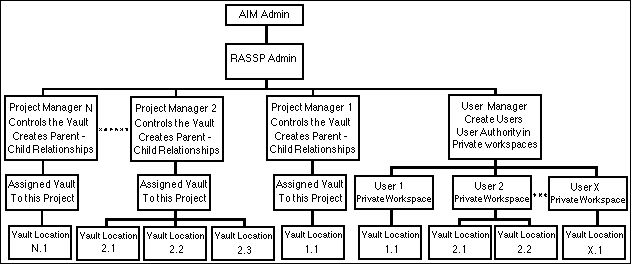
The AIMAdmin user commands the most authority over the RASSP Enterprise Framework. From his/her position in the hierarchy, he/she may perform any available action on any object, and thus perform the actions defined for any other user in the system. AIMAdmin controls and defines the RASSP environment. The RASSPAdmin user has limited super user authority. The RASSPAdmin can perform actions which govern the RASSP environment without being able to change the existing rules that define it. RASSPAdmin may perform the actions of all users in the system except the AIMAdmin user.
The User Manager grp is a group of assigned users that governs and maintains the user accounts in the RASSP environment. RASSPAdmin, or AIMAdmin, must assign a user to the User Manager position. The User Manager commands authority over all the user accounts in the system. From his position in the hierarchy, he may perform any action available in any user account. This is a useful feature when conditions arise where users are unavailable due to vacation, sickness, or other absence.
The Project Mgr grp is a group of assigned users that control an instantiated project in the RASSP environment. The RASSPAdmin or AIMAdmin must assign a user to the Project Mgr grp. By doing this, a project manager is created. Each project manager is all powerful within the context of that project and maintains the associated Project Vault in the system.
The Project grp, and its associated rules, are created when the RASSPAdmin instantiates a new project. It is a group of users assigned to support an instantiated project in the RASSP environment. The project manager, (or RASSPAdmin or AIMAdmin) must select an existing user from the user grp, and assign that user to the Project grp. By doing this, the project manager has added a user to the project support group. Members of a project create design objects and are allowed to share these objects by placing them in the associated project vault.
The user grp is a group of users that exist in the RASSP environment and are available for assignment to the User Manager grp, Project Mgr grp, or Project grp. The User Manager, (or AIMAdmin or RASSPAdmin) must create new users, validate them on the appropriate Host(s), and place them in the user grp. The user grp commands the least authority in the administrative hierarchy.